Application Control

While it’s commonly known that firewalls and antivirus are required to prevent cyber-attacks, many organizations feel that’s all that’s required to protect sensitive data from hackers. You must think like a hacker in order to safeguard your IT infrastructure against assault. Hackers can penetrate your surroundings in a variety of ways. The hackers are approaching these business difficulties from various angles. Owners of businesses should do the same.
CMMC 2.0 Self-Assessments Reality| Snap Tech IT

With the capacity to conduct self-assessments for Level 1 and a subset of Level 2, CMMC 2.0 delivers substantial improvements and sighs of relief to many Defense Industrial Base contractors. While this alleviates a significant load in many ways, there is a downside to these changes.
CMMC 2.0 Announcement in Upcoming Webinar

Snap Tech IT CEO, Karl Bickmore, Discusses CMMC 2.0 Announcement in Upcoming Webinar TEMPE, Ariz., November 15, 2021 – “Making sense of the latest changes to the CMMC Program can be challenging for DoD contractors. That’s why I’m excited for this opportunity to unravel what we’ve learned from the announcement as Snap Tech IT continues to educate, […]
How CMMC 2.0 Changes Affect DoD Contractors
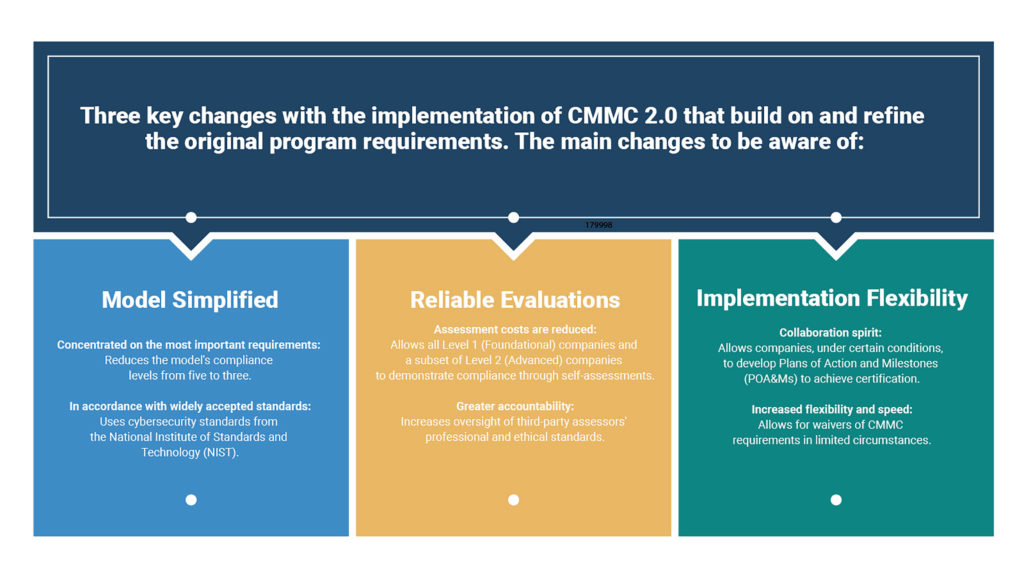
Announcing CMMC 2.0: An Overview of Changes With the implementation of CMMC 2.0 announced November 4, 2021, the Department of Defense is introducing several key changes that build on and refine the original CMMC program requirements. While significant changes have been made, we are still awaiting the approval of several requirements in the program. The […]
Financial Cybersecurity Readiness Webinar
Want to learn how to protect your business from debilitating cyber-attacks? Check out this educational video on how Snap Tech IT changed the cybersecurity game for Versant Capital, including key takeaways you can use today!
IDG Webinar – SMB IT Security. Protect your organization.
In this IDG Webinar – SMB IT Security, IDG explores IT decision-makers’ perspectives on cybersecurity. Watch the webinar & learn how manage, to detect, and respond to attacks.
Colonial Pipeline Cyber-Attack: Understanding the Threat

With the recent fallout surrounding the Colonial Pipeline breach felt across much of the country, I think it’s important that businesses embrace key takeaways on the techniques used in this attack and heighten our sense of awareness to detect when things are going wrong in our environment. Educating ourselves on the many shared techniques of […]
Consulting Firm

The Firm had a very familiar problem that a lot of companies have, Bandwidth. With no true IT department or security policy in place, they were left vulnerable to cyber-attacks.
Cybersecurity Solution Brief

A 360 degree look at Cybersecurity — Threats and the strategies to prevent, disrupt and respond to them. Learn about topics such as Cybersecurity Readiness, Statistics & Trends, SMB & Enterprise IT Struggles, Cyber Threats To Keep An Eye On and more.