CMMC 2.0 Announcement in Upcoming Webinar

Snap Tech IT CEO, Karl Bickmore, Discusses CMMC 2.0 Announcement in Upcoming Webinar TEMPE, Ariz., November 15, 2021 – “Making sense of the latest changes to the CMMC Program can be challenging for DoD contractors. That’s why I’m excited for this opportunity to unravel what we’ve learned from the announcement as Snap Tech IT continues to educate, […]
How CMMC 2.0 Changes Affect DoD Contractors
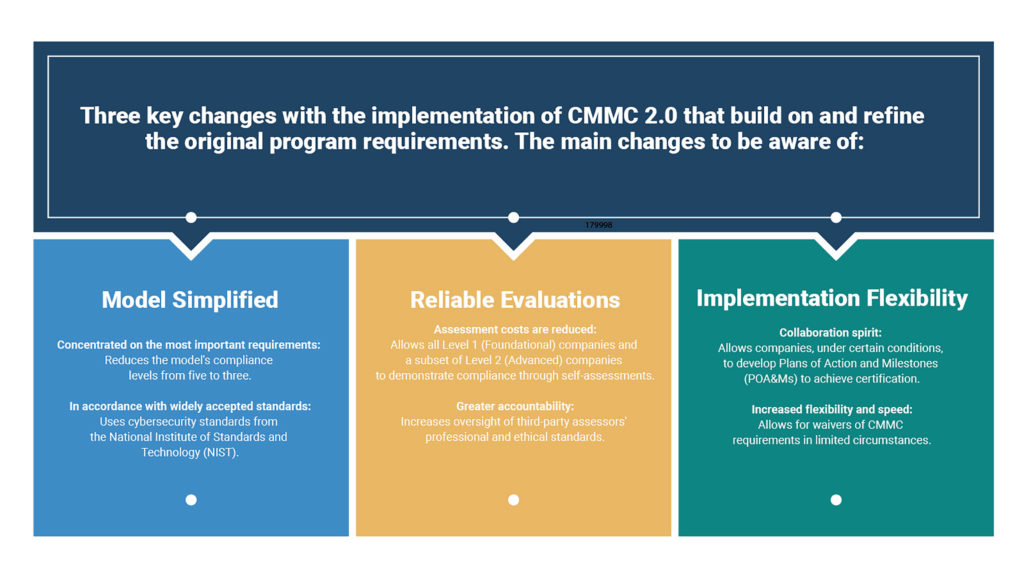
Announcing CMMC 2.0: An Overview of Changes With the implementation of CMMC 2.0 announced November 4, 2021, the Department of Defense is introducing several key changes that build on and refine the original CMMC program requirements. While significant changes have been made, we are still awaiting the approval of several requirements in the program. The […]
Costs of CMMC Compliance

Cost of CMMC Compliance: What You Need to Know With all of the hoopla swirling around the U. S. Department of Defense’s (DoD) decision to implement the Cybersecurity Maturity Model (CMMC,) as a requirement for future federal contracts, many contractors & subcontractors are contemplating the cost estimate around achieving the standard for certification. Contractors and subcontractors working […]
Case Study – Security & SEC Regulations

Because the firm must adhere to SEC regulations, it was imperative that their IT providers understand the regulation & compliance rigors that must go on with data security. With IT security as a leading concern, the firm found themselves having to offer IT security recommendations to their previous provider. The firm was concerned about regulatory red flags being missed.
Protect Yourself Against Cyber Thieves While Shopping

Shopping 101: Safeguarding Personal Information From online shopping to in-store purchases, cyber thieves have multiple ways of stealing your information and using it for their own financial gain. Here are a few protective steps you can take. Step 1. Ensure that any online company you are making purchases from has a verified and secured network. […]
Financial Cybersecurity Readiness Webinar
Want to learn how to protect your business from debilitating cyber-attacks? Check out this educational video on how Snap Tech IT changed the cybersecurity game for Versant Capital, including key takeaways you can use today!
IDG Webinar – SMB IT Security. Protect your organization.
In this IDG Webinar – SMB IT Security, IDG explores IT decision-makers’ perspectives on cybersecurity. Watch the webinar & learn how manage, to detect, and respond to attacks.
Virus Alert: How to Protect Your System from Lnkr Vulnerability

Did you know that there is a new type of cybersecurity threat that your Antivirus and Firewall won’t catch? As we began implementing threat detection in our internal systems, we discovered a new type of security threat that a firewall or antivirus is unlikely to catch. It’s known as Lnkr vulnerability and its currently making […]
Colonial Pipeline Cyber-Attack: Understanding the Threat

With the recent fallout surrounding the Colonial Pipeline breach felt across much of the country, I think it’s important that businesses embrace key takeaways on the techniques used in this attack and heighten our sense of awareness to detect when things are going wrong in our environment. Educating ourselves on the many shared techniques of […]