Malware and Viruses: What You Need to Know to Protect Your Data

By Karl Bickmore, CEO Snap Tech IT The terms “Malware” and “Virus” are used interchangeably in the computer world. While most people understand that both will create havoc on your system, they don’t necessarily know the differences between them. One of the best ways to protect your business data from both predators is to learn […]
Social Engineering
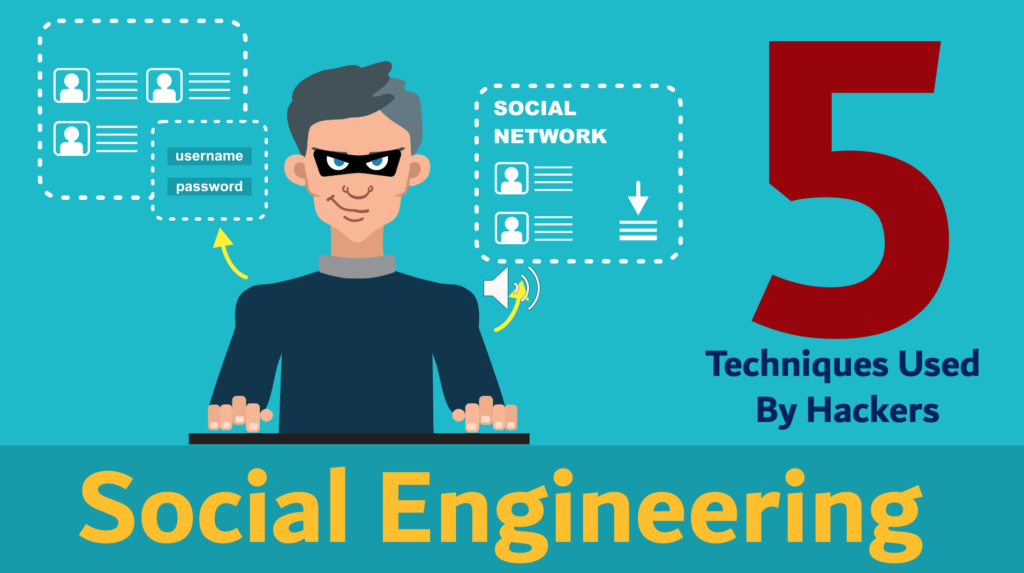
Increased sophistication of social engineering makes it difficult to know when you’re being had. Don’t fall for their tricks & see 5 techniques hackers are using to steal your data.
The Top 4 Ways Malware Is Spread

Every day, a company is infected with some form of malware. The Internet is a new battlefield; we’re in a cyberwar, hackers are the enemy and malware is the weapon.
Ransomware

Ransomware is an ever-evolving form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. check out the tips & tricks you need to know to stay safe.
Top 4 Phishing Stats of 2020 & Your Best Lines of Defense

Phishing is the first delivery method for other types of malicious software. A phishing attack isn’t just targeted at
gaining information. but they can also be used to distribute malicious programs, such as ransomware.
Why a Robust MDR Solution is a Top Priority in 2021

According to Gartner— 50% of organizations will be using Managed Detection and Response services for threat monitoring, detection, and response functions that offer threat containment capabilities.
Protecting Your Data from Cybercriminals

In a post-pandemic world, businesses are understanding the true value behind IT expertise & management of cybersecurity.
Five Reasons Why You Need to have a Recovery Plan in Place

Downtime & recovery from a security breach not only impacts your business financially but operationally as well
The Top 4 Ways Malware Is Spread

By: Shawn Brown, COO, Snap Tech IT Every day, I read another article about a company or city that has been infected with some form of malware. Which is any software program purposely designed to interfere with the normal functioning of a computer system for malicious reasons, such as to hold files hostage for ransom. One […]