Microsoft Copilot Demo: Everything You Need To Know About Copilot – Webinar Recording
A culture of cybersecurity doesn’t just happen. Learn how to build a culture of cybersecurity in your organization by watching our on-demand webinar.
Cybersecurity Awareness Month: How to Build a Culture of Cybersecurity – Webinar Recording

A culture of cybersecurity doesn’t just happen. Learn how to build a culture of cybersecurity in your organization by watching our on-demand webinar.
How Defense In Depth Will Save Your Business From Cybersecurity Breaches and Data Loss – Webinar Recording

Explore strategic ways to get more out of Microsoft Teams. Learn how to organize your Teams experience to improve communication across your company helping you to become a Microsoft Teams power user.
Watch this on-demand webinar to learn the Top 10 Tips to Get the Most Out of Microsoft Teams.
Snap Tech IT’s 2024 Outlook
Join us we look forward to the new year in “Snap Tech IT’s 2024 IT Outlook.” The IT landscape is poised for critical changes, impacting businesses of all sizes and across industries. This webinar is your opportunity to gain valuable insights into the technology trends and strategies that will shape the IT landscape in the coming year.
Ask a Hacker How New AI Tools are Making Hackers Even More Dangerous

In today’s digital landscape, the evolution of artificial intelligence (AI) and machine learning (ML) technologies has not only revolutionized businesses but has also empowered cybercriminals with advanced tools and techniques. Join us for an intriguing webinar, “Ask a Hacker,” where we delve into the fascinating world of AI-driven hacking and discuss how these emerging technologies are enabling cybercriminals to become even more dangerous.
Seven Key Steps to Securing Remote Workers
In today’s rapidly evolving work environment, remote work has become crucial for many organizations. However, with this increased flexibility comes a heightened need for robust security measures to protect sensitive data and mitigate potential cyber risks. Join us for an insightful webinar as we explore the seven key steps to securing remote workers effectively.
In this webinar, we will explore: How to assess remote work risks, Why identity and access management (IAM) is one of the most important cybersecurity considerations and so much more.
Comprehensive Risk Assessment Process
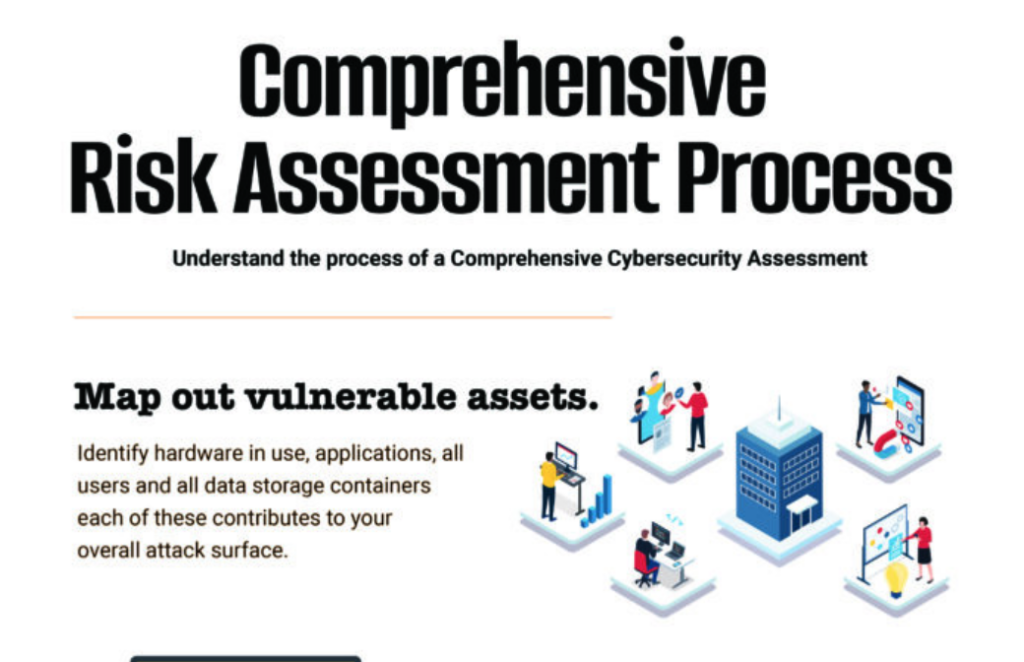
Understand your Vulnerabilities Assessments of security risk require a methodical approach that begins with knowing your critical security gaps. One of the best ways to identify those critical gaps is to complete a no-cost Rapid Security Snapshot that pinpoints top risk areas that leave your environment exposed to damaging cyber threats. With your Rapid Security […]
Exploring the Security Posture of Legal Firms

The American Bar Association’s 2021 Legal Technology Survey Report shines a light on security gaps among small to medium-sized firms that expose vulnerabilities, leading to sensitive data breaches, loss of billable hours & reputational damages. Explore key findings & learn simple tips to neutralize your risk.
Zero-Click
The cyber-attacks threat continues to intensify for businesses all across the United States. A method known as Zero-Click hacking is becoming increasingly prevalent, often pushed by governments onto individuals and activist groups. This is key, since phones are often the method of entry, which, in many cases, is tied to system networks. Learn more about how these attacks work and what you can do to minimize your risk exposure.