
Tips to Boost Security on Zoom Meetings
Zoom meeting use has increased dramatically in the past several years, but so have security concerns. Learn tips and tricks to keep your meetings secure.

Zoom meeting use has increased dramatically in the past several years, but so have security concerns. Learn tips and tricks to keep your meetings secure.

7 Cybersecurity Practices for Legal Firms By: Karl Bickmore, COO, Snap Tech IT Handling sensitive data that attracts hackers and malicious insiders is part of

Cybersecurity attacks are evolving, becoming more sophisticated, more frequent, and much more widespread, leading to elevated operational risks to banks and financial firms as a whole.

More than most types of business, financial management firms carry a heavy burden to avoid cybersecurity risk and protect their clients’ sensitive information. This is
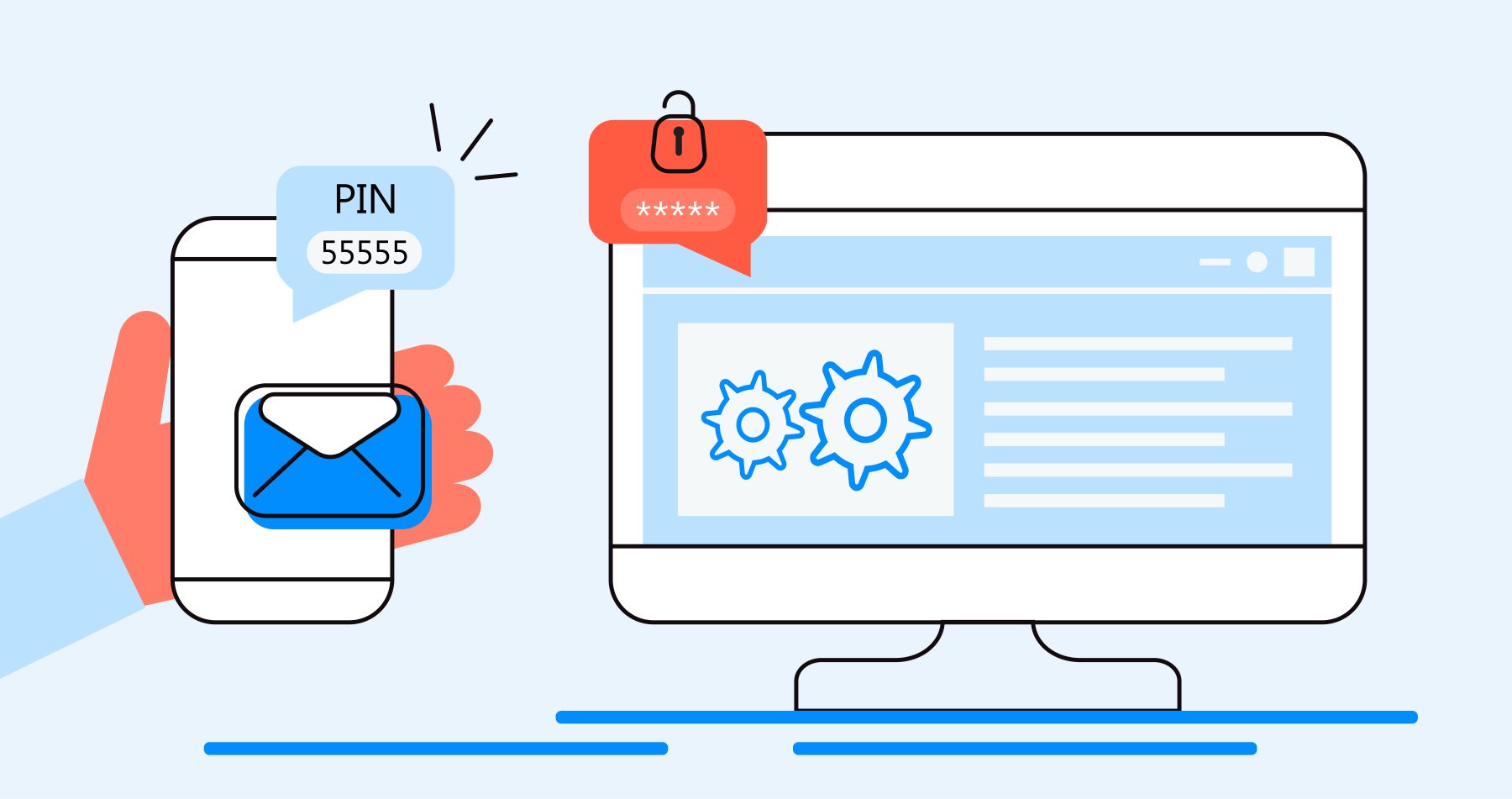
As businesses take necessary steps to shore up security in their environments, one of the most critical tools out there comes to mind as a must-have for anyone looking to keep the hackers out is multi-factor authentication. Authentication, in its simplest form, is the process of confirming that someone attempting to enter your environment is who they claim to be. Protecting your IT environment and sensitive data depends on knowing exactly who is trying to gain access.

By: Karl Bickmore, CEO, Snap Tech IT Whenever I come across a useful new tool on the market that I think might benefit our customers, I’m

Web Security at a Glance: Firewall Fundamentals by Karl Bickmore When was the last time you got into your car without fastening your seatbelt? That was

While it’s commonly known that firewalls and antivirus are required to prevent cyber-attacks, many organizations feel that’s all that’s required to protect sensitive data from hackers. You must think like a hacker in order to safeguard your IT infrastructure against assault. Hackers can penetrate your surroundings in a variety of ways. The hackers are approaching these business difficulties from various angles. Owners of businesses should do the same.

With the capacity to conduct self-assessments for Level 1 and a subset of Level 2, CMMC 2.0 delivers substantial improvements and sighs of relief to many Defense Industrial Base contractors. While this alleviates a significant load in many ways, there is a downside to these changes.
18 Bartol Street Suite 183
San Francisco, CA 94133
415-970-0100